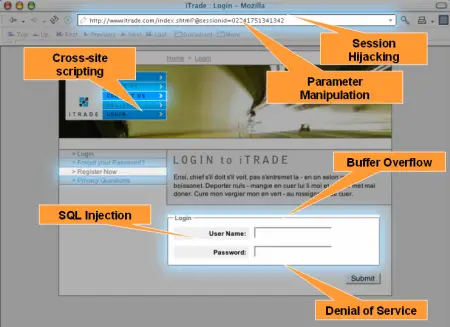
Website Threats and Their Effects or Capabilities
It is a profitable business for hackers to steal people’s data and use it for personal gains. The gains can be monetary or abstract. While hacking, phishing, and social engineering are common methods, hackers also use other people’s websites to compromise users’ computers and access their data. The following image gives you an idea of website threats. It is, therefore, a webmaster’s job to make sure his or her website is free of any malicious code and vulnerability. That is not an easy job considering that there might be thousands of pages and the hacker selectively inserts the code on some pages. Since it is a matter of your reputation, you have to do it. Fortunately, there are some tools available that can scan your websites daily to present you with a report of infectious code and vulnerability points (like login screens, forms, etc.). In addition, browsers and browser plugins are available that trigger an alarm when you are about to visit a malicious, infected website. Though you might have visited that site before, and though it might be hard for you to believe that a site you trust is infected, it may really be malicious without the webmaster knowing it – because an hour earlier, some hacker added some code to the site. Speaking of worst-case scenarios – or capabilities of website threats – there are two major sides of damage:
Common Types of Website Threats
The most common and noticed is clickjacking. In this method, a transparent layer of malicious code sits on a button or video. When you click on the button, it downloads the code to your computer. You might have seen similar methods for advertising on C-grade websites, mostly related to piracy and adult content, etc. Website redirection vulnerabilities enable hackers to use the redirections for their gains. They can either intercept data being exchanged or use the redirection to redirect users to a phishing site. Among other types of websites, threats are targeted attacks using readymade exploit kits available easily on the Internet. These kits enable the hackers to target certain (types of) websites and add malicious links to them. Another method is to send emails to the website with malicious links that bypass the unsuspecting webmaster to make it a malicious website. The recent attacks on popular websites indicate that even the biggest websites are vulnerable. People who once lose their credentials are not likely to return to the site again. Imagine your business or e-commerce website getting blacklisted and you are left in dark for weeks until the search engines whitelist them again. While the process to get a website removed from blacklists is tough, can your business survive if it is not on the public view for weeks? Read: How to remove Coinhive crypto-mining script from your website.
How to keep websites secure
Up-to-date software: Keep your website server software fully updated and patchedSSL Certificates: The companies offering safety certificates check your website before issuing the certificate of trust. The green part on the address bar next to “https” provides some assurance to the users of the website.Encryption: Use a secure connection for anything users do on your website, especially if involved in transactions.Upgrade to EV SSL: Do this in any part of the website where the customer may enter dataDaily Malware Scan: You can use products that scans your website pages for malware without reducing their load time. This way, you can remove the malicious code – in case it is there – before users are affected.Weekly Assessment of Vulnerabilities: Check for possible points of vulnerabilities and implement additional security there.
The above are just a few tips for securing your website. It explains threats to websites and their capabilities in brief. Now read: How to secure a WordPress site. Later today, we will read about Drive-by downloads and in a few days about how to keep a WordPress website secure.